More than 22.7 million U.S. businesses are one-man or one-woman shows. Each of these tiny firms has a single owner, but no paid employees at all. The US government calls these businesses “Nonemployer” businesses.
If you are one of those 22.7 million U.S. businesses, you probably know about Google Apps for Work, the professional email, online storage, shared calendars, video meetings, voice telephone service and more, built for business, by Google.
More than 5 million businesses have gone Google. You may be a Google Apps for Work single user and account holder. If so, you need to know about Google’s account access problem.
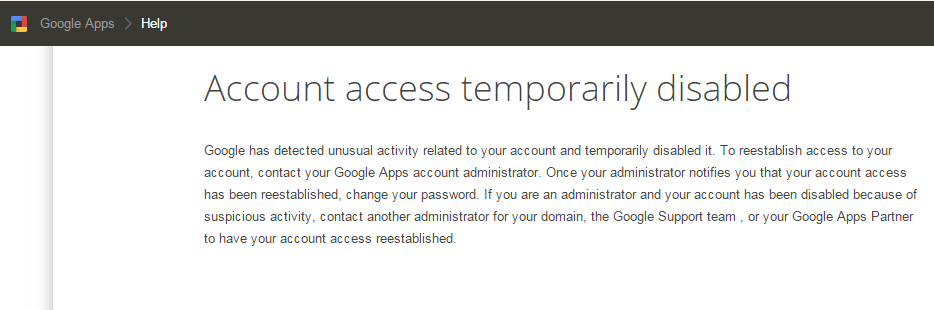
You may have experienced or will experience in the future the dreaded “Account access temporarily disabled” message when you log in to your Google Apps for Work account. Imagine your business’ risk if you depend on all of Google Apps for Work’s services including business telephone service and you find your Google Apps for Work account arbitrarily disabled. You can be out of business in the blink of an eye.
Google’s account access problem lies in it’s “catch 22” process to re enable your account, should you find yourself out of business. It goes like this;
Upon attempting to log on to your Google account, you get Google’s version of the “Blue Screen of Death”
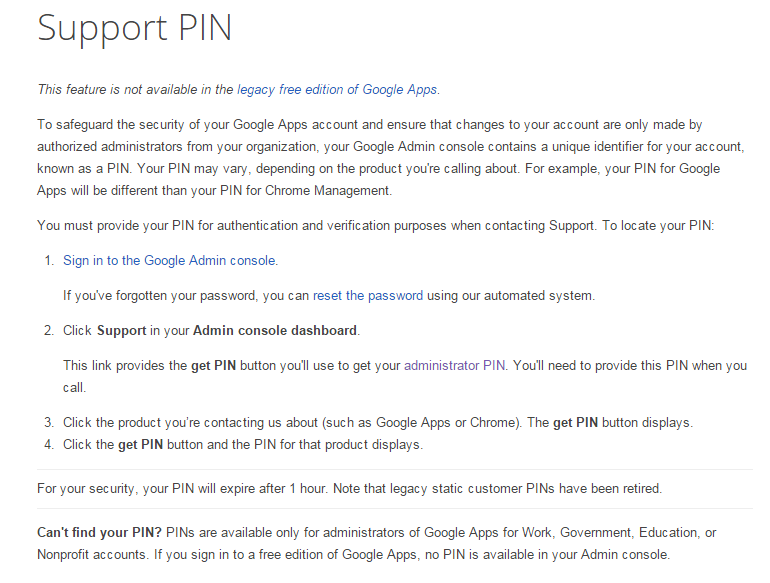
Since you are the only administrator, you seek the “24/7 phone and email support,” that you pay $5 to $10 a month for, from the “Google Support team”
Unfortunately, you cannot email support because you cannot access the “Admin Console.” But, you would want to call the “Google Support team” anyway because of the urgency to re enable your Google account. So you go about the business of locating your PIN because the “Google Support team” requires your PIN in order for them to answer their telephone. But, you see a page that states, “To locate your PIN: Sign in to the Google Admin console.”
So now, you’re stuck. You cannot call or email the “Google Support team” without access to your disabled Google account for their email link or PIN. That’s some strange paid “24/7 phone and email support.”
Fortunately, when Google’s account access problem happened to me, I located an obscure form at https://support.google.com/a/contact/admin_no_access that opened a support ticket. Unfortunately, 48 hours into the support request, my Google Apps for Work remains disabled.
Let me be the first to say that I like Google Apps for Work’s features and general performance. I especially like the ability to wipe a lost smartphone. I also like using Google Voice for calls using a computer headset. I’m not a Google Apps for Work reseller, but I have set up many businesses with Google Apps for Work.
But, single user Google Apps for Work accounts require a different approach. What can one do to protect one’s self from Google’s lackluster Google Apps for Work support?
- Google Apps for Work “Nonemployer” business folks should always have two admin users in their account, with strong passwords and be well documented. The second admin user can be used to re enable the primary admin user when that user experiences “Account access temporarily disabled.”
- Never use a Google Voice number as your primary business telephone number. If you have done that, immediately port your number out of Google Voice to a more dependable carrier, either a local telco service provider or a national VOIP provider with a demonstrated excellent support track record.
- Back up your primary user’s email, contacts, calendars, tasks, voice calls, chats, drive and any other data you may have in Google Apps for Work. One can use Outlook sync for manual and limited backup or go the distance with backupify, the leader in Google Apps backup.
Have you been stunned by the dreaded “Account access temporarily disabled” message? If so, what was your experience?
Update 11.26.2014: The account was re enabled at 5:30am, four days after the initial disabling. Once I correct the DNS workaround that will flow my email back into the account, if will be an entire week down, a service level that I would understand for free services, but not a paid business service. Also, my android phone was rendered useless during the process because the policy app on the phone. I’m certainly glad that this was not a business related account. When a “Nonemployer” business person needs paid “24/7 phone and email support,” they deserve not to wait a week. My conclusion, I will seriously reevaluate Google Apps for Work for my businesses and will not recommend Google Apps for Work to any other “Nonemployer” business person.